Passkey Directory – FIDO Alliance
Passkeys.directory – 1Password
Unlock 1Password with a passkey (beta)
Melissa’s Passkeys presentation for Tucson Macintosh Users Group
Passkey Directory – FIDO Alliance
Passkeys.directory – 1Password
Unlock 1Password with a passkey (beta)
Melissa’s Passkeys presentation for Tucson Macintosh Users Group
I hope you enjoy listening to the show as much as I did helping to make it. Allison and I could talk for days on this subject and I think you'll be able to tell. :)
Here are the show notes I composed for this episode. It's super long and I've modified it to add some new tips I thought of after the recording, but I hope it can be used as a reference guide for those who might be struggling or need some additional tips when working with their loved ones or assisting a friend in need.
Alternative HTML5 Audio PlayerProblem to be Solved: simplifying a complicated device to meet the basic needs of a user with limited touch interface skills while helping to preserve their autonomy in the process.
Recurring things I have observed to be helpful
If it causes more problems than it solves, it’s time to reevaluate.
This is not a complete list and it can take days or even weeks of tweaking, exploring, and experimenting to get someone’s device set up to be the most optimal for their needs, but it’s a good place to start thinking about the most necessary features and settings. Start by doing the initial setup and then make adjustments as the person you're helping gains more confidence and experience. If there is something they don’t like, take time to listen to their needs.
In the beginning it can be really hard for them to ask for help when they don’t know what something is called in order to phrase the question effectively. Aim to reduce whatever is causing friction by asking them what task they’re trying to accomplish. Maybe the text is too small or the screen doesn’t stay lit long enough for them to finish their question, but they weren’t sure how to convey that to you.
Always check and ask for consent as you go. They might not understand what it is they are consenting to though, so try to explain your intent to help them be more secure with their new device and how the setup is intended to help them use it more easily and securely. Trust is paramount and they’re relying on you to help.
Hacking and scamming incidents are on the rise. It’s a sad fact of pandemic life now, but on episode 351 of Geekiest Show Ever, we’re here to tell you that you can take back some control if you know what to look out for and how to implement best practices. We will give it to you straight because we believe that online security should be a regular part of our overall well-being. It’s why we so frequently discuss security issues and using password managers. Tune in to hear us share our field experience for ways to help your loved ones become safer in our digitally connected world.
 |
| Photo by Danielle MacInnes on Unsplash ⏯Audio file is here: http://www.mymac.com/podcast/GSE/GSE351.mp3 🎧 🦉Follow us for even more helpful information: |
Wow. 14 steps! They sure don't make it simple, do they Why do we even need Adobe Flash anyway?
It's one of those necessary evils that's called a plugin. It's like a supplement for our computers. Without it, we wouldn't be able to process certain multimedia content like videos or interactive graphs. Lots of banking websites still require it to make their websites function the way they were designed to be viewed by the visitor. They want to display information in a chart and it may have some type of animation. To you it may be overkill, but to the web designers, this is the choice they made.
What if I don't care about updating it? Can't I just skip it?
Sure, but you do so at your own risk. You could be allowing the plugin you are currently using to operate with a "hole" in it — one the bad guys could get through to compromise your security. Better safe than sorry.
Update: I published this piece in April when our second iPhone had been stolen by a student in a classroom several months prior. I am happy to report that I have successfully recovered the stolen iPhone! I did keep pinging it by using Lost Mode to send a message to the screen, and finally someone decided to text me and tell me they "found" it. Long story short, the iPhone was allegedly "purchased from a friend" and the person's girlfriend tried to restore it and discovered the message. We had to "pay off" this individual for a small sum of money, but we got the phone back and no data was lost or compromised. We had changed passwords just to be safe. I will write more about this story in another post because I learned a lot more about the recovery process, but I want to do some more penetration testing to document it properly. This will involve temporarily sacrificing one of the kid's iPhones then restoring it. Hey, drills are important though, right? It appears as though enabling Lost Mode removed the data from the phone, because when we got it back, it had been wiped with just my Lost Mode message on the screen. Did it get wiped when someone attempted to restore it using iTunes? It had been locked the whole time, so we're pretty sure data stayed safe as it passed between several middle-schoolers, but I still want to play hacker and see. Stay tuned!
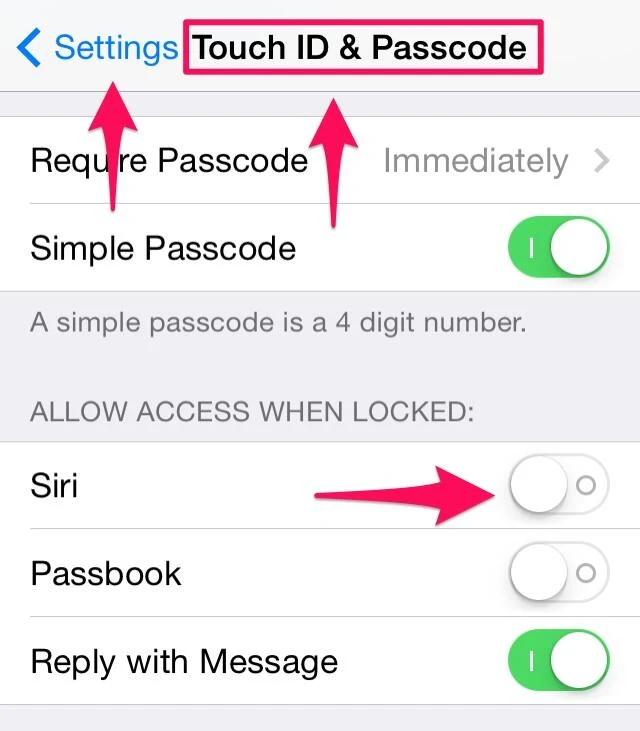
 This means a thief has from the time they pilfer your phone until you initiate Lost Mode to mine your sensitive information by getting Siri to spill the beans on you. If the thief disables connectivity by enabling Airplane Mode or disabling Wi-Fi or both, then Siri from the lock screen will no longer work, but your iPhone will show as offline when you try to track it. At this point, you better hope the thief hasn't taken notes.
This means a thief has from the time they pilfer your phone until you initiate Lost Mode to mine your sensitive information by getting Siri to spill the beans on you. If the thief disables connectivity by enabling Airplane Mode or disabling Wi-Fi or both, then Siri from the lock screen will no longer work, but your iPhone will show as offline when you try to track it. At this point, you better hope the thief hasn't taken notes. Have you heard about the Heartbleed Bug in the news? You may have seen its logo plastered across your screen at some point. I wonder if sales of antacid are on the rise right about now because I bet it's causing a lot of heartburn lately. If you are not overly concerned with this news at the moment, I'm not here to send you into a panic, but identity theft can really take its toll if you're not prepared. I know from experience and it's not the sort of thing I wish on anyone.
Have you heard about the Heartbleed Bug in the news? You may have seen its logo plastered across your screen at some point. I wonder if sales of antacid are on the rise right about now because I bet it's causing a lot of heartburn lately. If you are not overly concerned with this news at the moment, I'm not here to send you into a panic, but identity theft can really take its toll if you're not prepared. I know from experience and it's not the sort of thing I wish on anyone.